Table of Contents
Key Takeaways
- Chameleon launched in late 2014 as Browz.io, making it the oldest antidetect browser still in active development
- We built one of the first Chromium-forked antidetect solutions and watched detection systems systematically dismantle it over the following years
- The pivot to real browser management (2019) came from necessity, not marketing — the fork approach was dying
- Modern detection happens at the TLS/transport layer, before fingerprint spoofing code even executes
- The trajectory matters: modified browsers degrade over time while real browser approaches improve
What Does “Oldest Antidetect Browser” Actually Mean?
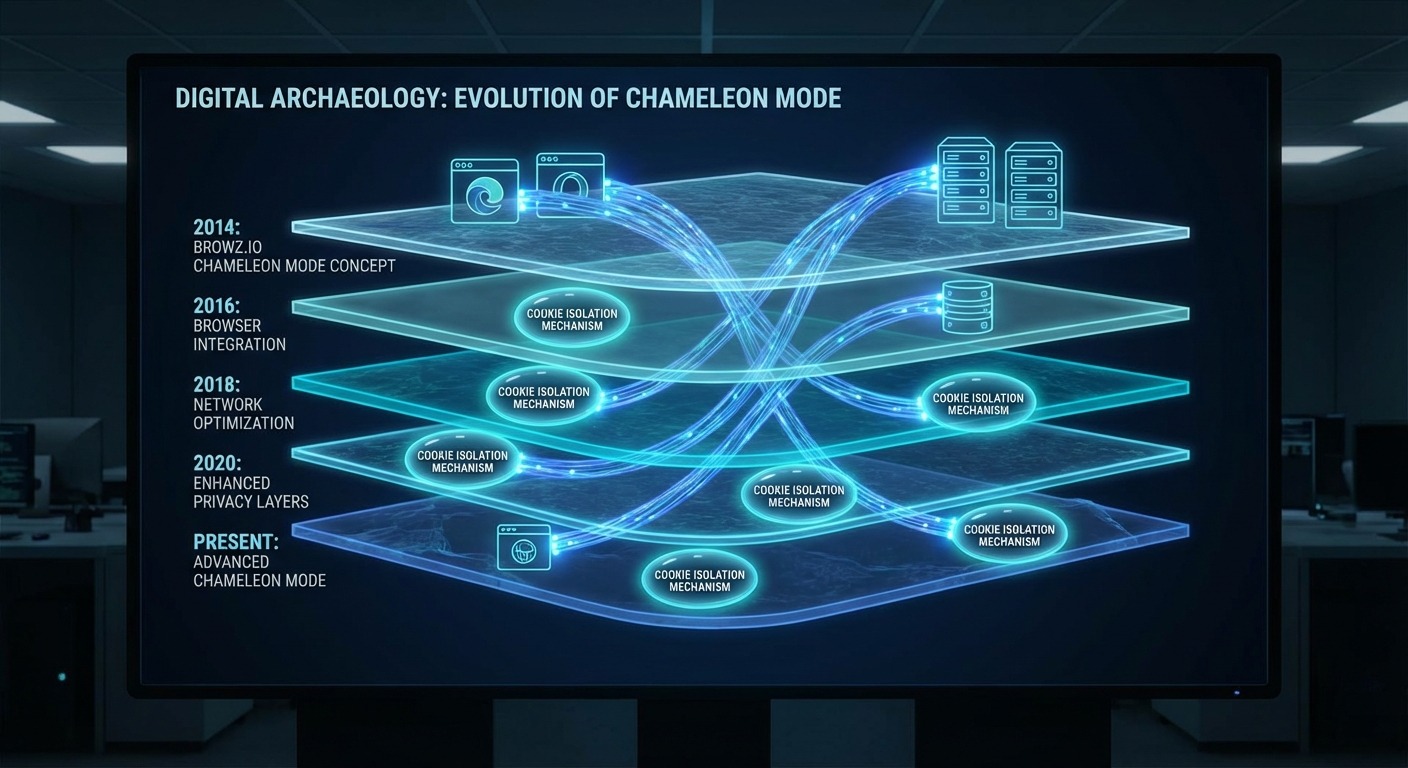
Chameleon Mode traces its lineage to late 2014, when we launched as Browz.io — an SEO productivity tool that evolved into one of the first dedicated antidetect browser solutions.
But here’s the thing most “oldest” claims won’t tell you: longevity in this space often means you’ve made more mistakes than anyone else. We have. And the biggest one was spending years perfecting an approach that detection systems were specifically designed to defeat.
This is the honest story of those ten years.
2014-2016: The Browz.io Era and the Birth of Browser Forking
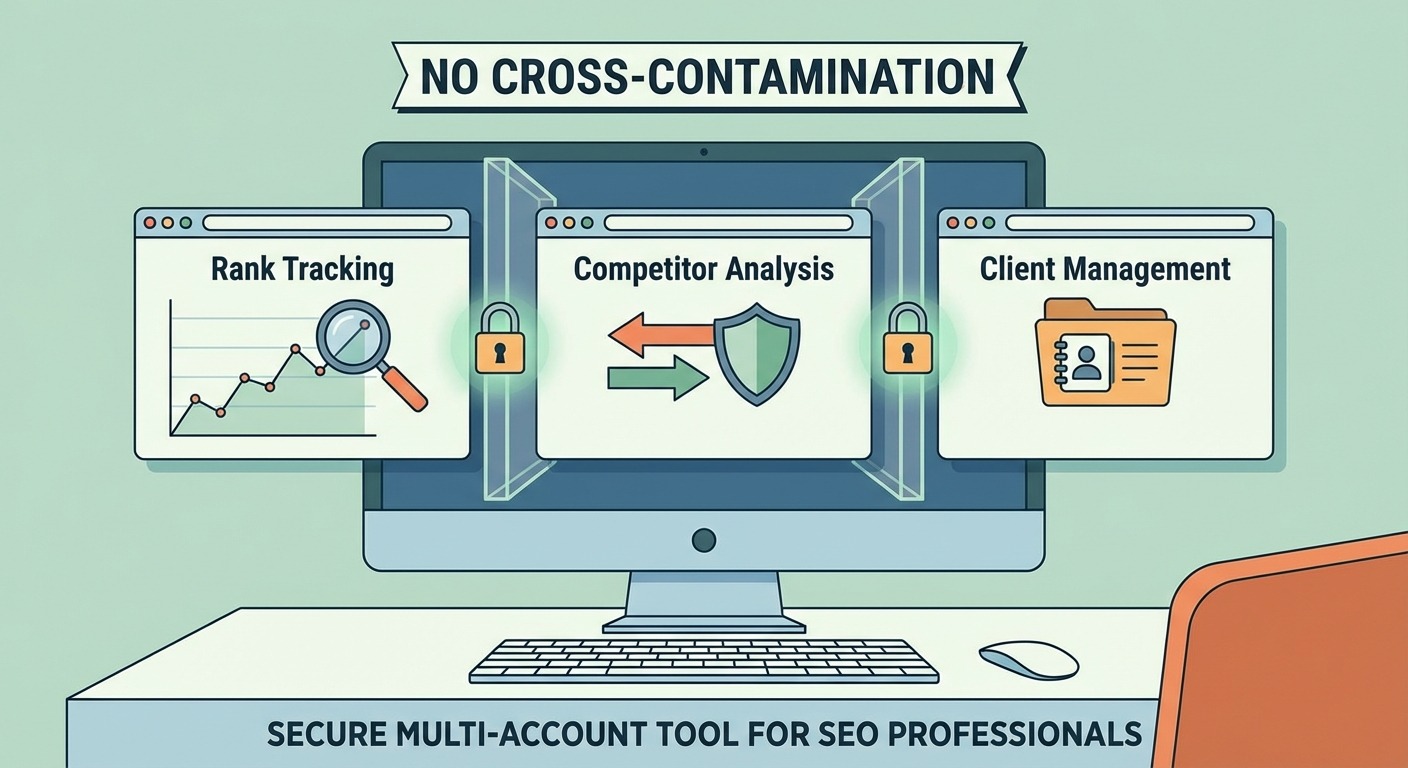
We started Browz.io in late 2014 as a tool for SEO professionals who needed to manage multiple accounts without cross-contamination. The problem was real: rank tracking, competitor analysis, and client management all required separate browser environments.
The solution seemed obvious. Fork Chromium. Modify the fingerprinting surfaces. Give each profile a unique identity.
We weren’t the only ones with this idea, but we were among the first to ship it. The early versions worked remarkably well. Detection in 2015 was primitive — platforms checked basic fingerprint consistency and called it a day. Our modified Chromium sailed through.
What we built:
- Custom Chromium builds with spoofed canvas fingerprints
- Spoofed WebRTC
- Modified navigator properties
- Isolated cookie and storage containers per profile
For about 18 months, this was genuinely cutting-edge. Clients scaled their operations. We scaled our team. Everything pointed up.
Then Google got serious.
2017-2018: The Detection Arms Race Begins
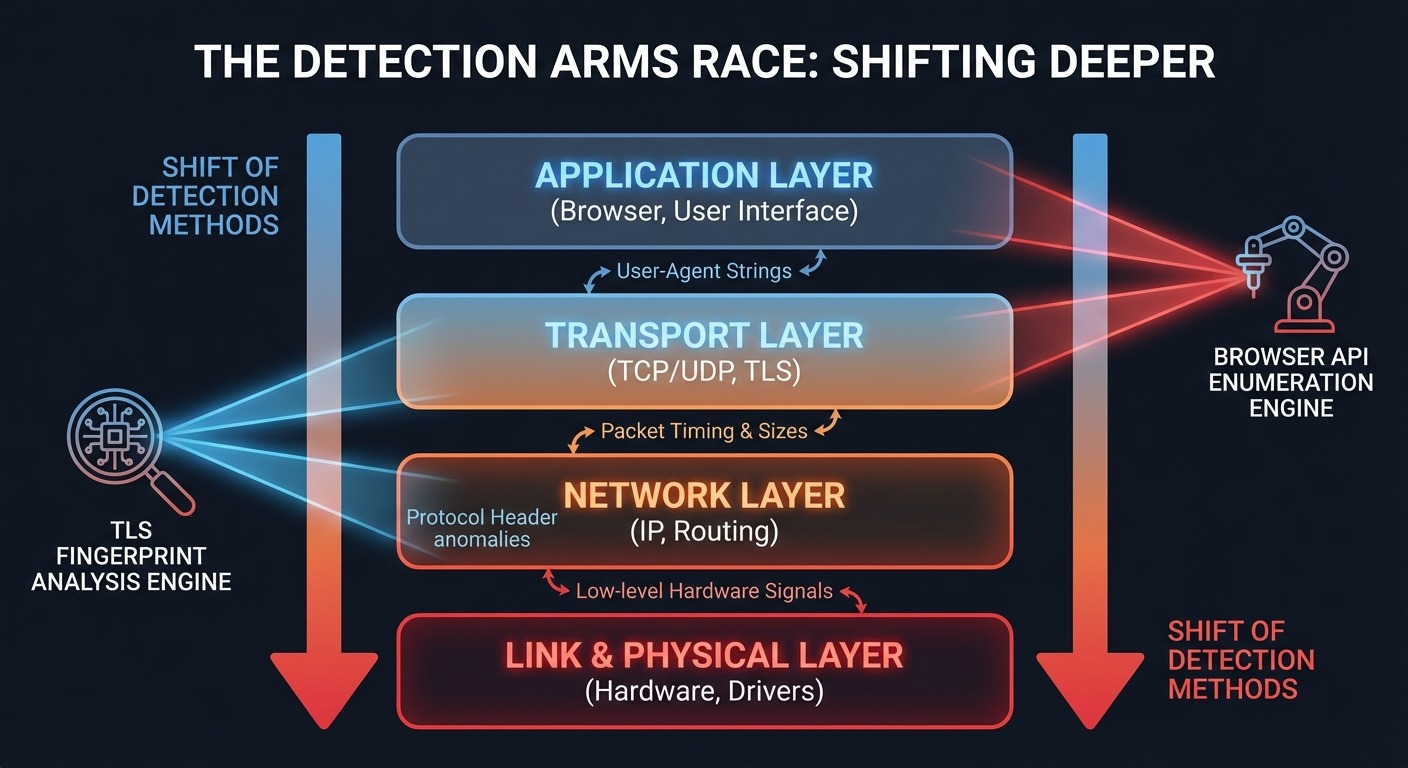
The shift happened faster than we anticipated. Platforms stopped relying on JavaScript fingerprinting as their primary detection method. They moved deeper into the stack.
Here’s what we observed:
| Year | Primary Detection Method | Our Fork’s Effectiveness |
|---|---|---|
| 2015 | Basic JS fingerprinting | High |
| 2016 | Canvas + WebGL checks | High |
| 2017 | TLS fingerprint analysis | Declining |
| 2018 | Build integrity + behavioral | Poor |
The problem wasn’t that our spoofing got worse. It’s that spoofing became irrelevant to the decision. Platforms started evaluating browsers at the TLS handshake — before our JavaScript modifications even loaded.
A modified Chromium binary produces a TLS fingerprint that doesn’t match any real Chrome version in the wild. JA3 fingerprinting made this trivially detectable. Our cipher suite ordering, our extension negotiations, our ALPN behavior — all slightly wrong. Close enough to fool a human. Not close enough to fool statistical analysis at scale.
We patched. We tweaked. We released update after update. The detection systems learned faster than we could adapt.
Why Did We Keep Pushing the Fork Approach?
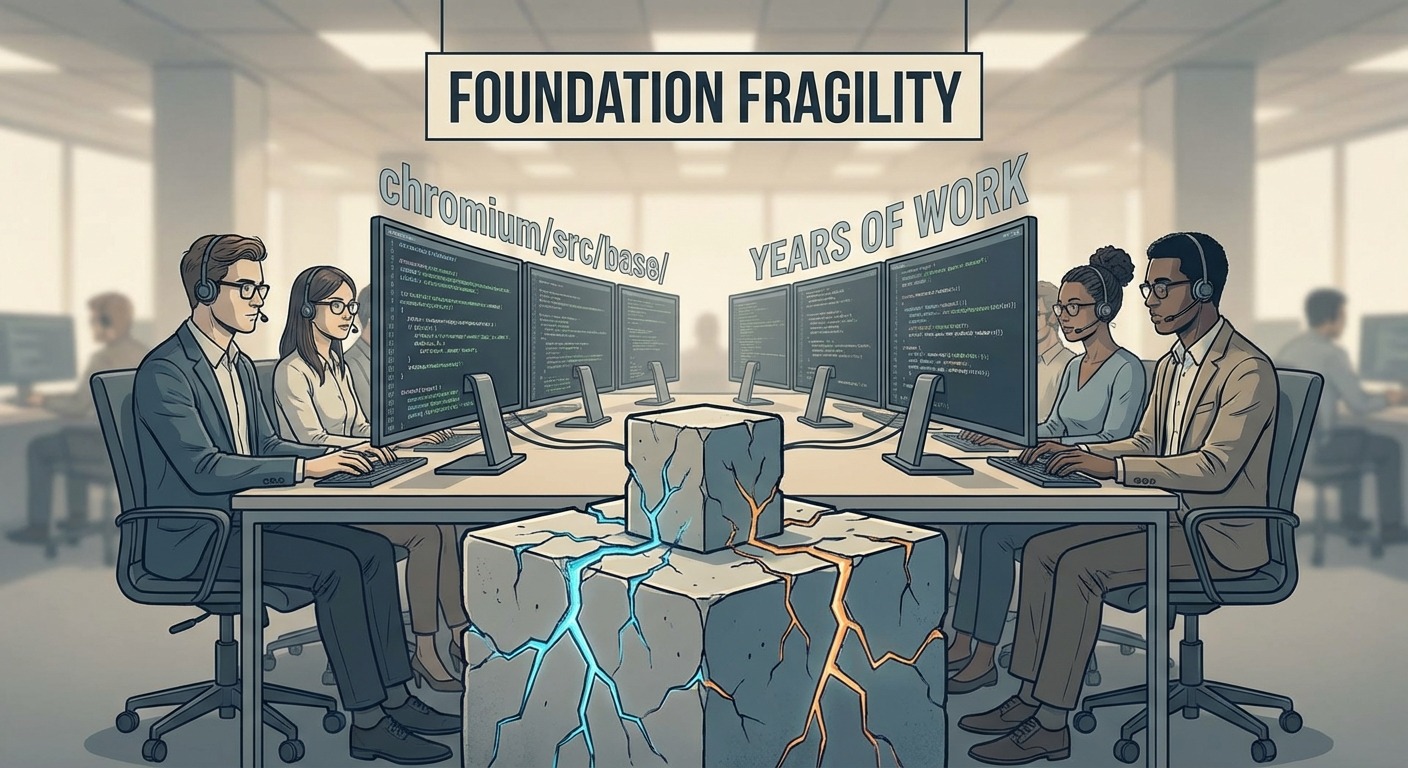
Sunk cost. Institutional momentum. The genuine belief that better engineering would solve it.
We had years of work in that codebase. A team that knew Chromium internals. Customers who expected the product they’d bought. Pivoting meant admitting the foundation was cracked.
So we doubled down. We added HTTP/2 fingerprint spoofing. We tried to match Chrome’s SETTINGS frame values. We implemented client hints consistency layers. Each patch bought us weeks, maybe months, before detection systems caught up.
By late 2018, we were releasing updates every two weeks just to maintain baseline functionality. Our engineering team spent more time chasing Chrome releases than building features. The modified browser approach had become a treadmill, and the speed kept increasing.
2019: The Pivot to Real Browser Management
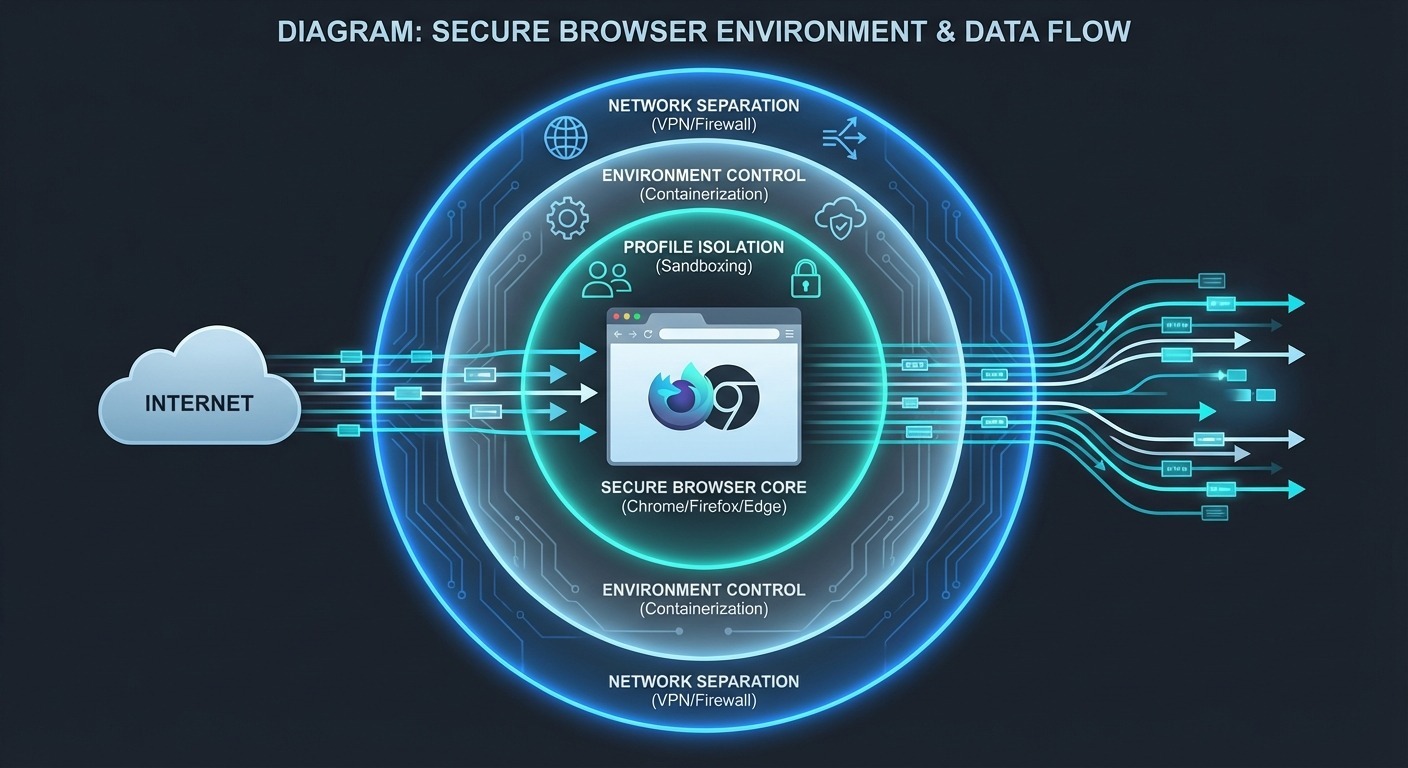
We killed the fork in 2019 and relaunched as Chameleon Mode with an entirely different architecture. Not because we wanted to. Because the data forced us.
The insight that changed everything: the most undetectable browser is the one that doesn’t need to lie.
Instead of modifying Chromium to spoof being a real browser, we asked a different question. What if we used actual, stock browsers — Chrome, Edge, Firefox — and controlled the environment around them instead?
The technical shift:
| Aspect | Old Approach (Fork) | New Approach (Real Browsers) |
|---|---|---|
| Browser binary | Modified, unsigned | Stock, vendor-signed |
| TLS fingerprint | Spoofed (detectable) | Native (identical to millions) |
| Updates | Manual patching | Automatic via OS |
| Detection surface | Growing | Shrinking |
Real browsers pass TLS checks because they ARE real browsers. Their JA3 fingerprint matches because it’s the actual Chrome JA3 fingerprint. Build integrity checks pass because the binary is vendor-signed and unmodified.
We stopped trying to create a convincing fake. We started managing authentic originals.
What “Environment Control” Actually Means

Chameleon Mode doesn’t touch the browser binary. We control everything around it:
- Profile isolation — Each identity gets its own cookies, localStorage, IndexedDB, completely separated
- Network separation — Independent connections per profile, no cross-profile correlation
- Geolocation sync — Location settings automatically match proxy location
- Timezone alignment — Temporal signals stay consistent with geographic identity
- Proxy integration — Per-profile or global, with automatic environment adaptation
The browser stays authentic. The environment creates the separation.
This sounds simple in retrospect. It took us five years of building the wrong thing to see it clearly.
2020-2024: Proving the Model
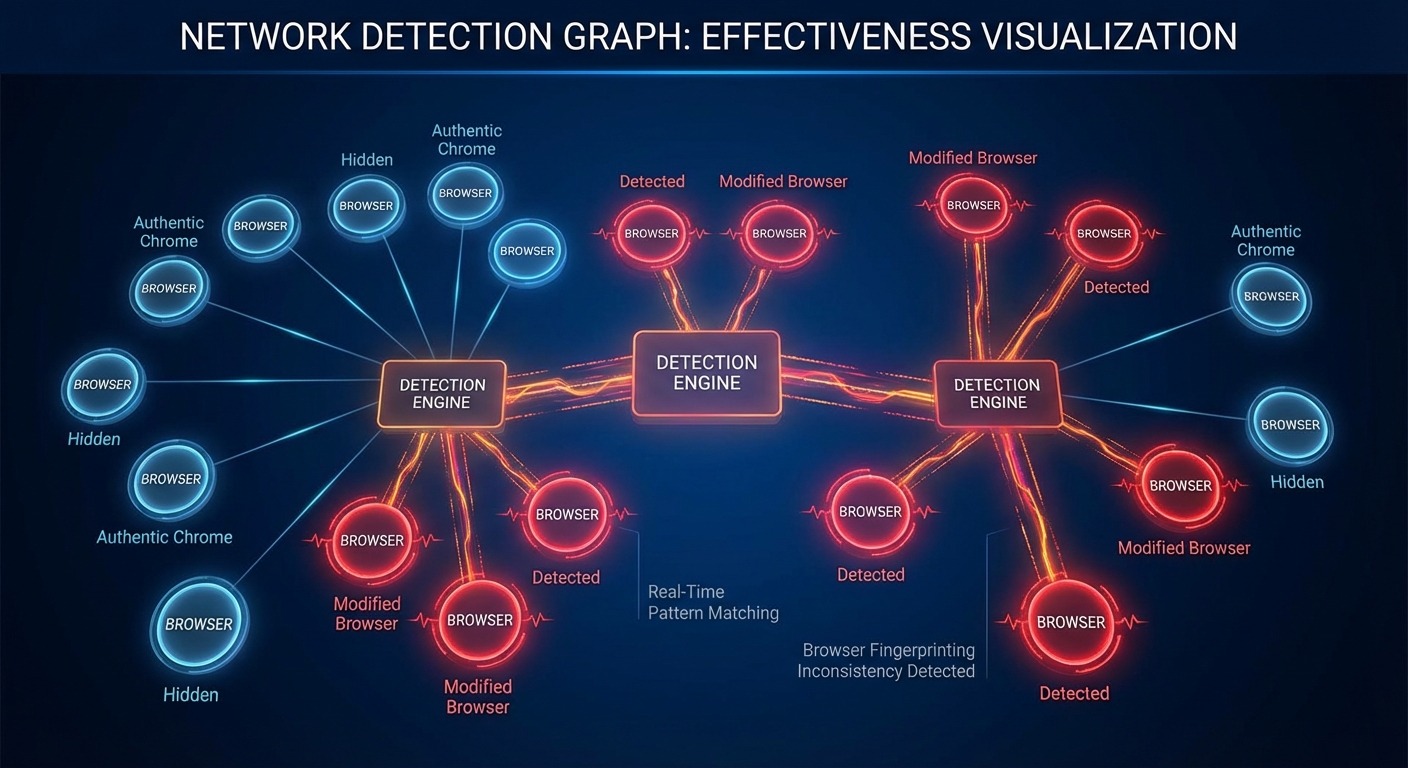
The years since the pivot have validated the approach. Not because we’re smarter than we were in 2017. Because the architecture aligned with how browser detection actually works.
What we’ve observed:
Detection systems have gotten dramatically better at identifying modified browsers. The fingerprinting-era tools — including our old fork — have seen steadily increasing burn rates. Every Chrome update creates new detection opportunities for platforms and new patching work for fork maintainers.
Meanwhile, the real-browser approach improves automatically. When Chrome updates, our users get the update through normal OS channels. Their TLS fingerprint stays current. Their protocol behavior matches the latest release. The detection surface shrinks without us shipping anything.
The trajectory argument isn’t marketing. It’s observable in the data.
What Ten Years Taught Us About This Industry

Lesson 1: Detection will always catch up to deception.
If your model requires fooling detection systems, you’re in an arms race you will eventually lose. The platforms have more resources, more data, and more incentive.
Lesson 2: Authenticity scales better than spoofing.
Real browsers don’t require patches when Chrome releases a new version. Real browsers don’t have cipher suite ordering bugs. Real browsers don’t fail build integrity checks.
Lesson 3: The pivot was the product.
Our decade of experience building the wrong thing taught us exactly why the wrong thing fails. That knowledge is baked into every architectural decision in the current product.
Who Chameleon Mode Serves Now
The same people we started with in 2014 — SEO professionals, digital marketers, agencies managing multiple client accounts, affiliate marketers scaling campaigns. The use cases haven’t changed. The reliability has.
Current capabilities:
- Up to 1,500 browser profiles (Pro plan)
- Full Playwright automation integration
- Team collaboration with role-based access
- Cross-device profile sync
- Automatic geolocation and timezone matching
The pricing runs $19-$199/month depending on profile count and team features. We offer a 7-day trial on the Basic plan.
FAQ
Q: Is Chameleon Mode actually the oldest antidetect browser?
A: Yes. We launched as Browz.io in late 2014 and have operated continuously since. The product has evolved dramatically, but the lineage is unbroken.
Q: Why did you abandon the Chromium fork approach?
A: Detection moved to the transport layer. Modified browsers fail TLS fingerprint analysis before JavaScript even executes. The fork approach stopped working reliably around 2018.
Q: What browsers does Chameleon Mode support now?
A: Firefox, Chrome, and Brave — stock, unmodified versions that update through normal OS channels.
Q: Is the real-browser approach actually more effective?
A: For transport-layer detection, yes. A real browser’s TLS fingerprint is identical to millions of legitimate users. There’s nothing anomalous to detect.
Q: What happened to users of the old forked browser?
A: We migrated them to the new architecture in 2019. Profile data transferred. The underlying technology changed completely.
Resources
- TLS fingerprinting methodology: Salesforce Research — JA3 (GitHub)
- Client hints specification: W3C Client Hints Infrastructure (w3.org)
- HTTP/2 fingerprinting research: Akamai Security Research (akamai.com)
- Browser build integrity: Chromium Security Documentation (chromium.org)
- Detection evolution timeline: Internal Chameleon Mode data, 2015-2024












