Table of Contents
Key Takeaways
- Incognito mode and VPNs don’t isolate accounts—they share browser fingerprints, WebRTC leaks, and font lists across sessions
- Reddit and Quora detect linked accounts through 47+ browser signals, not just IP addresses
- The container method creates fully isolated browser environments where each account operates as a separate identity
- Chameleon Mode uses real, unmodified browsers with environment-level control—the only approach that passes transport-layer detection
- Team workflows require simultaneous access without triggering 2FA cascades or session invalidation
The Problem Nobody Talks About
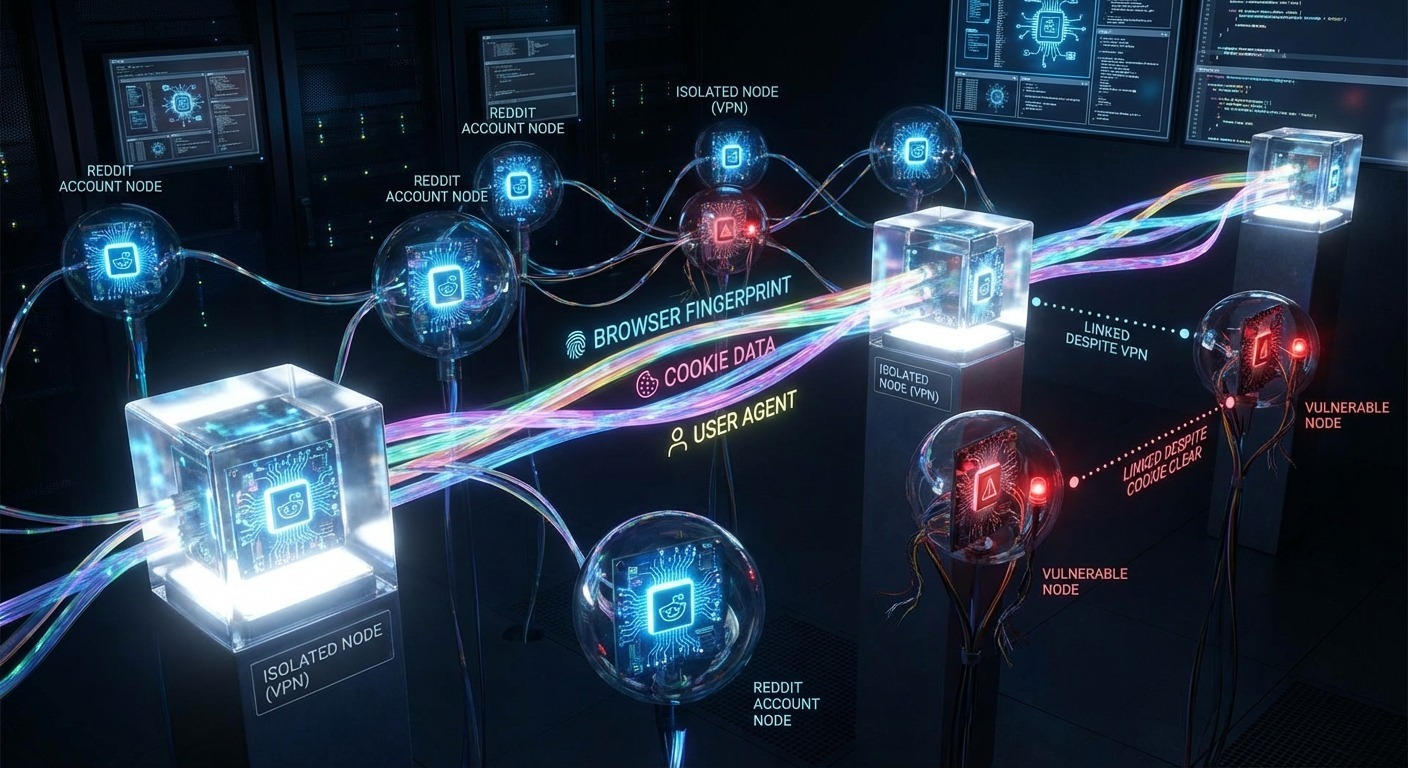
Most advice on managing multiple Reddit & Quora accounts is dangerously outdated. It assumes platform detection still works like it did in 2019—check the IP, maybe look at cookies, call it a day.
That world is gone.
I’ve watched marketers, community managers, and agency teams burn through accounts for three years now. The pattern is always the same: they follow “best practices” from blog posts written by people who’ve never managed more than two accounts. They use incognito mode. They rotate VPNs. They clear cookies religiously. And then, six weeks later, every account they’ve touched gets flagged within 72 hours of each other.
The accounts weren’t linked by IP. They weren’t linked by cookies. They were linked by browser fingerprint—a unique signature that incognito mode doesn’t touch, VPNs don’t mask, and cookie clearing doesn’t affect.
This article explains the container method: how to actually isolate identities at the environment level so platforms can’t correlate them. We’ll cover why traditional approaches fail, how to set up proper isolation, and how teams can share access without creating detection cascades.
If you manage multiple Reddit accounts for clients, brands, or communities—or you’re doing the same on Quora—this is the only approach that works long-term.
Why Incognito Mode & VPNs Leak Data (WebRTC & Font Lists)

Incognito mode is privacy theater. It hides your history from your spouse. It does nothing against platform detection systems.
Here’s what incognito mode actually does:
- Creates a temporary session without access to your main cookies
- Doesn’t save browsing history to your profile
- That’s it. That’s the entire feature.
Here’s what incognito mode doesn’t do:
- Change your browser fingerprint
- Mask your installed fonts
- Hide your screen resolution
- Block WebRTC IP leaks
- Alter your canvas fingerprint
- Modify your AudioContext signature
- Prevent timezone correlation
When you open two incognito windows and log into different Reddit accounts, both sessions have identical fingerprints. Reddit’s detection system sees the same browser signature hitting their servers from two “different” accounts. The correlation happens instantly.
The 47 Signals Problem
Modern platform detection uses dozens of signals simultaneously. IP address is just one—and increasingly, it’s not even the most important one.
| Signal Category | Examples | Incognito Protection? |
|---|---|---|
| Network | IP address, WebRTC local IP | No (WebRTC leaks) |
| Browser | User agent, vendor, platform | No |
| Graphics | Canvas fingerprint, WebGL hash | No |
| Audio | AudioContext signature | No |
| Fonts | Installed font list | No |
| Screen | Resolution, color depth, pixel ratio | No |
| Timing | Timezone, language, locale | No |
| Hardware | CPU cores, device memory, GPU | No |
| Behavior | Mouse movement, typing cadence | No |
Every incognito window inherits all 47+ signals from your base browser. You’re not creating separate identities. You’re creating separate sessions of the same identity.
Why VPNs Make It Worse
VPNs solve one problem—IP address—while creating two new ones.
Problem 1: Datacenter IP Ranges
Most VPN providers route traffic through known datacenter IP ranges. Reddit and Quora maintain databases of these ranges. Traffic from datacenter IPs triggers elevated scrutiny automatically.
Residential users don’t browse from AWS or DigitalOcean. When your “home user” account logs in from a datacenter IP, that’s a signal.
Problem 2: Geographic Inconsistency
Your VPN says you’re in Chicago. Your timezone setting says America/Los_Angeles. Your browser language is en-GB. These inconsistencies don’t happen with real users. They only happen with people trying to mask their location.
Platforms don’t need to prove you’re using a VPN. They just need to flag accounts with inconsistent signals for additional verification. The friction alone kills productivity.
Problem 3: Session Timing
You switch VPN servers. Your IP changes from Chicago to Miami. But you never disconnected from Reddit. Your session continues uninterrupted despite an “impossible” geographic jump.
Real users don’t teleport. Their sessions don’t survive 1,000-mile relocations. This pattern is trivial to detect.
WebRTC: The Leak Everyone Ignores
WebRTC is a browser protocol for peer-to-peer communication. Video calls use it. Screen sharing uses it. And by default, it exposes your real IP address to any website that asks—even through a VPN.
Here’s the sequence:
- You connect to VPN (IP: 203.0.113.45)
- You visit Reddit
- Reddit’s JavaScript calls WebRTC STUN servers
- WebRTC returns your local IP (192.168.1.15) and your real public IP (98.76.54.32)
- Reddit now knows your VPN IP and your real IP
The VPN didn’t fail. WebRTC bypassed it entirely.
Some VPN clients block WebRTC. Most browser extensions that claim to block it don’t work consistently. And even if you successfully block WebRTC, you still have 46 other signals linking your accounts.
Font Fingerprinting: The Signal You Can’t Hide
Your operating system has fonts installed. Some came with the OS. Some you added. The specific combination of installed fonts creates a near-unique fingerprint.
Detection systems test which fonts your browser can render. They don’t ask for a font list—they measure rendering behavior. There’s no permission prompt. There’s no way to block it without breaking websites.
A Windows machine with default fonts, Adobe Creative Suite, and Microsoft Office has a font fingerprint that matches roughly 2% of users. Add one unusual font—a free download you grabbed for a project three years ago—and you’re identifiable.
Incognito mode uses your system fonts. VPNs don’t affect fonts. Cookie clearing doesn’t remove fonts. The only way to change your font fingerprint is to use a different browser environment with different installed fonts.
The Container Method: Environment-Level Isolation

The container method treats each account as a completely separate browser environment. Not a separate tab. Not a separate window. A separate installation with its own fingerprint, storage, network configuration, and behavioral patterns.
This is the only approach that survives modern detection because it eliminates cross-contamination at every layer:
| Layer | Traditional Approach | Container Method |
|---|---|---|
| Cookies | Cleared between sessions | Isolated per profile |
| LocalStorage | Shared across sessions | Isolated per profile |
| Browser Fingerprint | Identical across sessions | Unique per profile |
| Network Path | Same IP or VPN | Separate proxy per profile |
| Timezone | System timezone | Matched to proxy location |
| Session State | Shared browser memory | Isolated memory space |
When you operate from properly isolated containers, each account appears to come from a different user on a different computer in a different location. Because functionally, it does.
Why Browser Modification Fails
Some tools try to achieve isolation by modifying the browser itself. They fork Chromium, patch the internals, and spoof fingerprint values to make each profile appear different.
This approach worked when detection was JavaScript-based. It doesn’t work anymore.
Detection moved to the transport layer. Before your page even loads—before JavaScript executes—platforms evaluate:
- TLS fingerprint: The signature of how your browser negotiates encrypted connections
- HTTP/2 behavior: Protocol-level settings that differ between real and modified browsers
- Binary integrity: Whether the browser binary matches what vendors ship
Modified browsers fail these checks because their TLS fingerprint doesn’t match real Chrome. Their protocol behavior has anomalies from patching. Their binaries fail integrity verification.
The browser lies, but the lie is detectable before it even gets to tell it.
Real Browser Management: The Chameleon Mode Approach
Chameleon Mode takes a fundamentally different approach. Instead of modifying the browser to lie about its fingerprint, it uses real, unmodified browsers and controls the environment around them.
The browser is stock Chrome, Edge, or Safari—vendor-signed, unmodified, identical to what millions of legitimate users have. The TLS fingerprint matches because it is the real TLS fingerprint. Protocol behavior is native because nothing was patched. Binary integrity passes because the binary was never touched.
What Chameleon Mode controls:
- Profile isolation: Each identity has its own cookies, localStorage, IndexedDB, and cache
- Network separation: Each profile can use a different proxy with no cross-contamination
- Timezone synchronization: Timezone automatically matches the proxy location
- Locale consistency: Language and regional settings align with geographic identity
- Storage boundaries: No data can leak between profiles
The browser stays authentic. The environment changes per identity. Detection systems see real browsers from real locations with consistent signals—because that’s exactly what they’re getting.
The Trajectory Argument
Modified browsers degrade over time. Every Chrome update creates new detection surface. Every patch to spoof fingerprints creates new anomalies. The approach is fundamentally fighting upstream—and upstream always wins eventually.
Real browser management improves over time. Browser updates happen automatically through the OS. New Chrome features are inherited immediately. As more people use stock browsers, your traffic blends with a larger population of legitimate users.
One approach requires constant maintenance and gets less effective yearly. The other requires no maintenance and gets more effective yearly.
Tutorial: Setting Up Isolated Profiles in Chameleon Mode
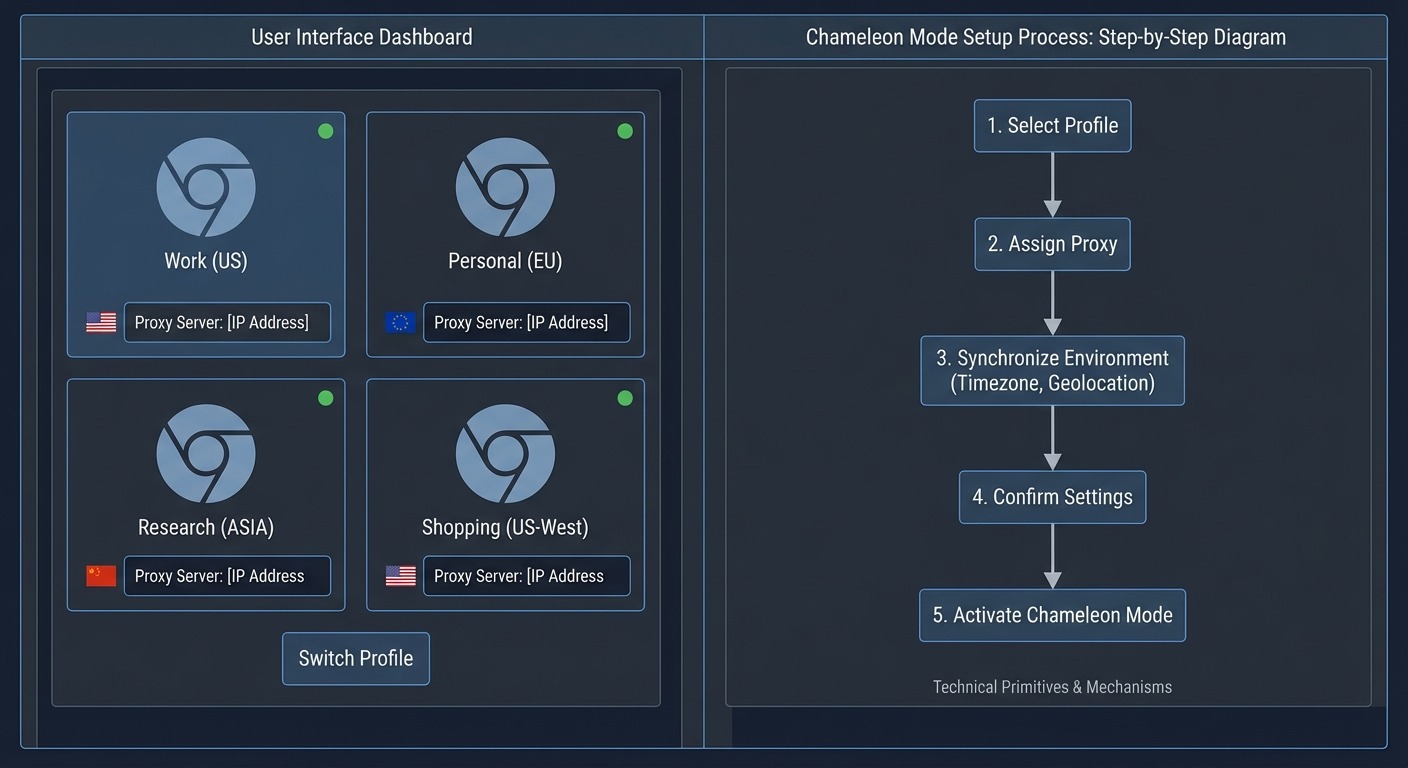
Setting up proper account isolation takes about 10 minutes per identity. Here’s the exact workflow.
Step 1: Create a New Browser Profile
From the Chameleon Mode dashboard, create a new profile for each Reddit or Quora account you’ll manage. Don’t reuse profiles across platforms for the same “persona”—Reddit and Quora can’t link accounts across platforms, but they can detect if multiple accounts on their platform share characteristics.
Naming convention matters for organization at scale. Use a consistent format:
reddit-client-acme-mainreddit-client-acme-backupquora-client-acme-thought-leadership
The tagging system lets you filter by client, platform, or purpose. When you’re managing 50+ profiles, this isn’t optional—it’s survival.
Step 2: Assign Proxy Configuration
Each profile needs its own network path. Never share proxies between profiles on the same platform.
| Proxy Type | Best For | Avoid When |
|---|---|---|
| Residential | Primary accounts, high-value identities | Budget is extremely limited |
| Mobile | Accounts needing mobile-realistic signatures | Desktop-only activities |
| Datacenter | Testing, disposable accounts | Accounts you need long-term |
Residential proxies route through real ISP IP addresses. They’re more expensive but indistinguishable from legitimate home users. For accounts that matter, this is non-negotiable.
Chameleon Mode’s flexible proxy integration supports per-profile assignment. Set the proxy once; the profile remembers it. No configuration on each launch.
Step 3: Automatic Environment Synchronization
Once you assign a proxy, Chameleon Mode automatically synchronizes environment signals to match:
- Timezone aligns with proxy location
- Geolocation returns consistent coordinates
- Language/locale settings match the region
You don’t configure these manually. The system handles consistency. This eliminates the signal mismatches that VPN users constantly trigger.
Step 4: Initial Account Setup
Launch the profile and navigate to Reddit or Quora. Create your account or log into an existing one.
Critical: Complete initial account setup in a single session. Platforms track “account age” signals:
- Time since creation
- Activity consistency from first login
- Geographic stability in early days
An account that’s created, ignored for two weeks, then suddenly active from a different location triggers review. Build some organic activity into each account during the first week.
Step 5: Profile Switching Workflow
To manage multiple Reddit accounts operationally:
- Open Chameleon Mode dashboard
- Click the profile for the account you need
- Browser launches with that identity’s complete environment
- Do your work
- Close when finished—session state saves automatically
Never have two Reddit profiles open simultaneously on the same machine, even in different Chameleon Mode profiles. The profiles are isolated, but you don’t want timing correlations in your activity patterns.
Step 6: Ongoing Maintenance
Each profile maintains its own:
- Cookie jar (login sessions persist)
- Browser history (platform can verify you’ve been there before)
- localStorage (site preferences, interface customizations)
- Cache (returning visitor patterns)
When you return to a profile after days or weeks, everything is preserved. The account looks like a returning user, not a fresh session—because it is a returning user, from that identity’s perspective.
Team Workflow: Sharing Access Without Triggering 2FA

Multi-person account management is where most teams break their accounts. Here’s why it happens and how to prevent it.
The 2FA Cascade Problem
Standard scenario:
- Marketing manager logs into client’s Reddit account from office
- Reddit sees: IP 203.0.113.45, Chrome on Windows, EST timezone
- VA in Philippines logs into same account
- Reddit sees: IP 180.191.xxx.xxx, Chrome on Windows, PHT timezone
- Reddit triggers 2FA verification
- Client receives verification code and asks what’s happening
- Trust erodes. Access gets revoked. Contract at risk.
Even when teams coordinate and share credentials properly, the location-hopping triggers security systems designed to catch account compromise.
Chameleon Mode’s Solution: Profile Sharing
Chameleon Mode’s team collaboration features solve this at the architecture level:
One-Click Account Sharing
Share any profile with team members instantly. They receive access to the complete environment—proxy assignment, saved cookies, browser configuration, everything.
When your VA in the Philippines opens the shared profile, they’re connecting through the same proxy as you. Reddit sees the same IP, same fingerprint, same everything. As far as the platform knows, it’s the same user continuing their session.
Simultaneous Multi-User Access
Multiple team members can access profiles concurrently. Chameleon Mode handles session coordination. The profile’s cloud-stored state synchronizes across devices.
This enables follow-the-sun operations. Your US team works EST hours. Your Philippines team takes over during US night. The account never sees a geographic shift because both teams access through the same network configuration.
| Team Location | Working Hours (Local) | Activity Window (Account’s Perspective) |
|---|---|---|
| New York | 9am-5pm EST | 9am-5pm EST |
| Manila | 9am-5pm PHT | 9pm-5am EST |
| Combined | — | Near-continuous “EST-based user” |
Role-Based Access Control
Not everyone needs full access to every profile.
- Admin: Full control, can modify proxy assignments and settings
- Operator: Can use profiles, cannot modify configurations
- Viewer: Can see profile status, cannot launch or operate
For agencies managing client accounts, this protects against misconfiguration. A junior team member can’t accidentally change a proxy assignment and trigger a location shift.
Automation Continuity During Sharing
If you’re running automated workflows through Playwright (Chameleon Mode’s built-in automation framework), sharing a profile doesn’t interrupt automation.
The automation runs in the cloud regardless of who’s accessing the profile UI. A team member can open the profile, check status, even do manual work—and the scheduled automation continues unaffected.
This matters for accounts with posting schedules, engagement workflows, or monitoring tasks. Sharing access for manual oversight doesn’t break automated operations.
Quora Specifics: Avoiding “Collapsed Answers”
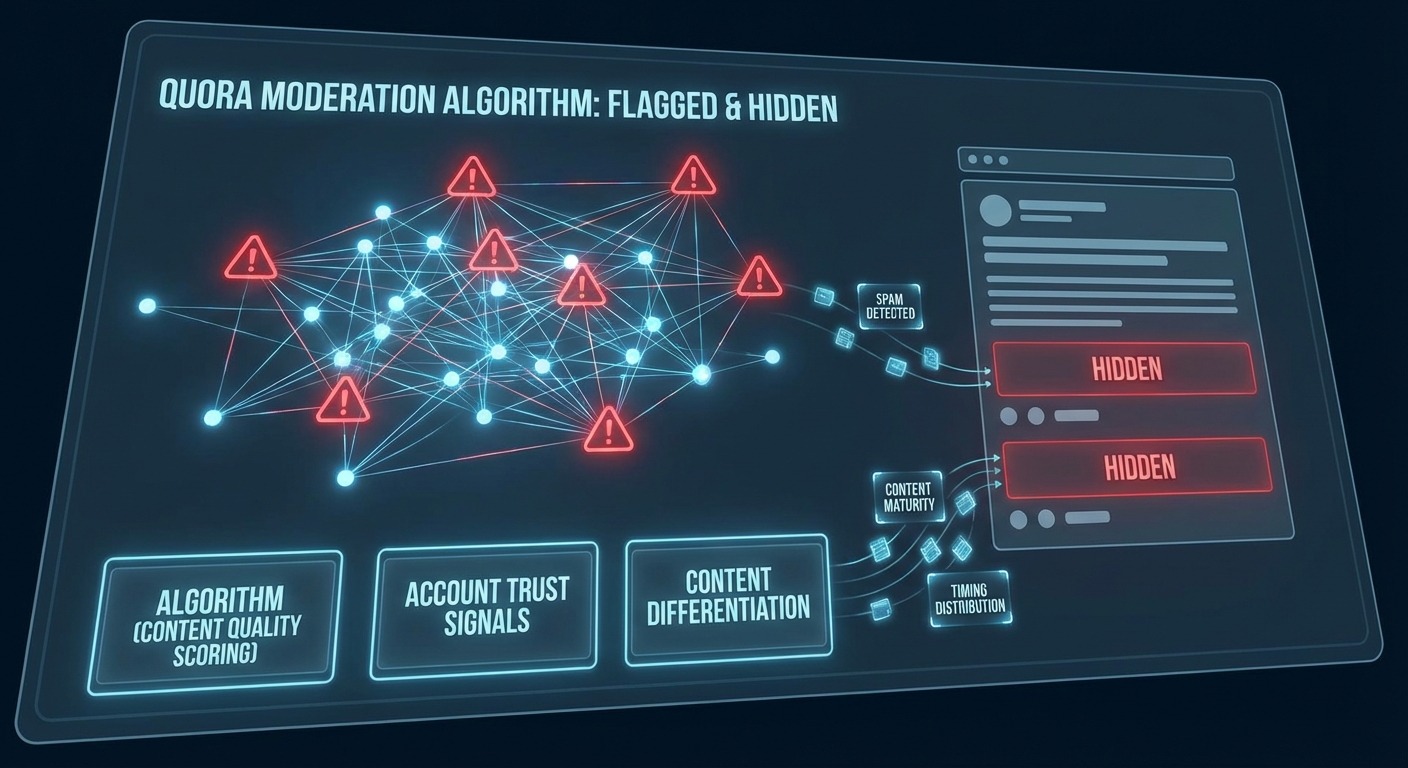
Quora’s detection is different from Reddit’s. Understanding the differences prevents wasted effort applying Reddit tactics to a platform with different rules.
How Quora Differs from Reddit
| Factor | Quora | |
|---|---|---|
| Account linking detection | Aggressive, automated | Less aggressive, more human review |
| Content quality scoring | Karma system, community-driven | Algorithm-driven, opaque |
| Penalty for detection | Shadowban, suspension | Collapsed answers, reduced distribution |
| Recovery difficulty | Hard to impossible | Moderate with behavior change |
Quora doesn’t ban aggressively. It suppresses. Your answers get “collapsed” (hidden behind a click). Your content stops appearing in feeds. You can still post, but nobody sees it.
This is worse than a ban in some ways. With a ban, you know something’s wrong. With collapsed answers, you can post for weeks before noticing your reach dropped to zero.
Why Answers Get Collapsed
Quora collapses answers based on several factors. Some relate to account management:
Low-Quality Signals
- Generic answers that could apply to any question
- Answers shorter than 100 words on complex questions
- Heavy promotional content without value
- Copy-pasted responses across multiple questions
Account Trust Signals
- New accounts with no profile completion
- Accounts that only answer, never ask or upvote
- Geographic inconsistency (timezone shifts)
- Activity patterns that don’t match human behavior
Spam Pattern Signals
- Multiple accounts answering the same questions
- Cross-linking between accounts
- Coordinated upvoting
- Identical or near-identical content across accounts
Container Method Adaptations for Quora
When managing multiple Quora accounts, the container method requires additional considerations:
Profile Maturity Requirements
Quora weighs account age and completeness heavily. Each profile needs:
- Complete bio with credentials
- Profile photo
- Topic follows (at least 20)
- Mix of questions asked, answers given, upvotes made
- Gradual ramp-up period (2-4 weeks before using for client work)
This maturation process must happen within isolated profiles. You can’t “warm up” an account in your regular browser and then transfer it to a containerized profile—the fingerprint shift will flag the account.
Content Differentiation
Reddit tolerates similar posting patterns across accounts if they’re in different subreddits. Quora does not.
If three accounts answer the same question, even with different wording, Quora’s algorithm detects the coordination. The answers collapse. Sometimes all three accounts get suppressed.
| Scenario | Reddit Approach | Quora Approach |
|---|---|---|
| Same topic, multiple accounts | Different subreddits, similar content OK | Different questions, unique angles required |
| Promoting same URL | Rotation across subreddits | One account per URL, varied positioning |
| Building authority | Karma farming, then promotion | Genuine expertise demonstration first |
Timing Distribution
Quora’s algorithm analyzes activity patterns. Five accounts all answering questions between 9-10am EST looks like a managed operation because it is one.
Distribute posting times across accounts. Use Chameleon Mode’s automation capabilities to schedule posts across a realistic activity window:
- Account A: Morning (8-10am)
- Account B: Midday (12-2pm)
- Account C: Evening (6-8pm)
- Account D: Weekend mornings
- Account E: Random weekday distribution
This doesn’t require manual scheduling. Playwright automation handles timing distribution programmatically.
The “One Good Account” Rule
For most Quora use cases, one well-maintained account outperforms five neglected ones.
Quora rewards consistent, high-quality participation more than Reddit does. A single account with 500+ answers, completed credentials, and steady activity has distribution power that five new accounts can never match.
Use multiple accounts for:
- Different client verticals (a healthcare account shouldn’t also promote SaaS)
- Backup/risk distribution for critical clients
- Testing answer positioning before using primary accounts
Don’t use multiple accounts to:
- Amplify the same content through fake engagement
- Answer the same questions multiple times
- Create artificial “debate” between your own accounts
Quora detects these patterns. The collapsed answer penalty is less obvious than a Reddit ban but equally damaging.
Advanced: Automation Workflows for Scale
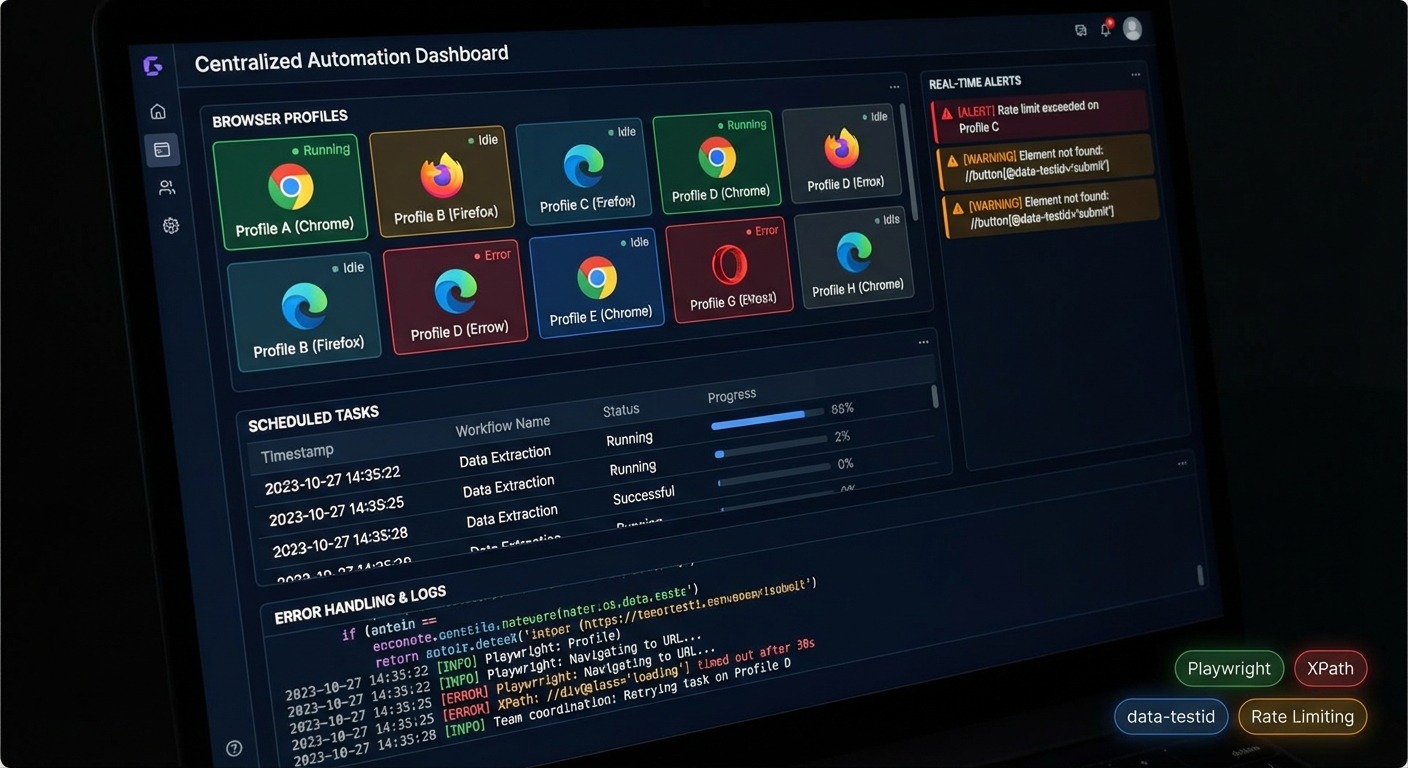
Manual account management doesn’t scale past 10-15 profiles. Once you’re managing more, automation becomes mandatory.
Playwright Integration
Chameleon Mode integrates with Playwright—the same automation framework used by enterprise QA teams and developers. This isn’t a proprietary scripting language. It’s industry-standard tooling.
What can be automated:
| Task | Automation Benefit | Manual Time Saved |
|---|---|---|
| Login checks | Verify sessions active, flag issues | 30 sec × profiles × daily |
| Content posting | Schedule across accounts and times | 5-10 min per post |
| Engagement | Upvotes, follows, comments | 2-3 min per action |
| Monitoring | Check for bans, warnings, notifications | 1-2 min per profile daily |
| Data collection | Export performance metrics | 10-15 min per account |
At 50 profiles, manual login checks alone consume 25+ minutes daily. Automation reduces this to a dashboard glance.
Building Reliable Workflows
Automation fails when it’s brittle. Here’s how to build workflows that survive platform UI changes:
Element Selection Strategy
Don’t select elements by:
- Exact XPath (breaks when DOM changes)
- Class names (often auto-generated, change frequently)
- Positional selectors (break when layout shifts)
Do select elements by:
- data-testid attributes (stable, meant for testing)
- Semantic roles (button, textbox, navigation)
- Text content (more stable than structural position)
Error Handling Requirements
Every automation workflow needs:
- Timeout handling (what if the page doesn’t load?)
- Element-not-found fallback (what if the UI changed?)
- Rate limiting (what if you’re making requests too fast?)
- Session recovery (what if login expired?)
Chameleon Mode’s Playwright implementation includes logging and monitoring. When a workflow fails, you know which step failed and why.
The 80/20 Automation Rule
Automate the 20% of tasks that consume 80% of time:
| High-Value Automation | Low-Value Automation |
|---|---|
| Session verification | Complex content writing |
| Scheduled posting | Nuanced engagement |
| Metric collection | Crisis response |
| Account monitoring | Strategy decisions |
Content generation still needs human oversight. Engagement that requires context still needs judgment. Don’t automate decision-making—automate execution.
Team Automation Coordination
With multiple team members running automations:
- Centralize scheduling: One calendar for all automated actions prevents overlap
- Log everything: Know which team member’s workflow made which action
- Stagger execution: Don’t have all workflows trigger at the same time
- Alert on failure: Team lead needs immediate notification when automation breaks
Chameleon Mode’s cloud infrastructure handles coordination. Workflows run server-side, not on team members’ local machines. Someone closing their laptop doesn’t stop scheduled tasks.
Risk Management: When Things Go Wrong
Assume you’ll lose accounts. Not because the container method fails, but because platforms change policies, make errors, or decide your content violates rules you didn’t know existed.
Detection Recovery Protocol
If an account gets flagged:
Step 1: Isolate Immediately
Don’t log into the flagged account from profiles you use for other accounts. If detection happened through fingerprinting (unlikely with proper isolation) or behavioral patterns, you don’t want to contaminate healthy profiles.
Step 2: Assess the Trigger
What changed before the flag?
- New content type?
- Different posting pattern?
- New team member accessing the account?
- Proxy provider issue?
Most flags come from content or behavior, not identity detection. Knowing the trigger determines whether you can appeal.
Step 3: Appeal or Abandon
| Situation | Action |
|---|---|
| Content policy violation | Appeal if borderline, abandon if clear violation |
| “Suspicious activity” warning | Wait 48 hours, reduce activity, monitor |
| Full suspension | Appeal once, then abandon |
| Shadowban | Abandon immediately, not worth recovery time |
Time spent recovering a shadowbanned account is better spent building a replacement. The account’s distribution power is already destroyed.
Redundancy Planning
For accounts that matter:
- Backup profile: Second account in same niche, maintained but not primary
- Content archive: Everything posted, stored externally for reposting
- Follower communication: Way to reach audience if primary account dies
The 50/300/1,500 profile limits in Chameleon Mode’s plans aren’t about having that many active accounts. They’re about having headroom for backups, testing, and replacements.
What Proper Isolation Prevents
The container method doesn’t prevent:
- Content-based flags (you posted something that violated rules)
- Behavioral pattern detection (you acted like a bot)
- Human review flags (someone reported you)
The container method does prevent:
- Account linking across identities
- Fingerprint-based correlation
- Session hijacking detection from location shifts
- Cross-contamination when one account is flagged
This is important. Isolation protects healthy accounts from infected ones. If Account A gets flagged, Accounts B through Z remain unaffected because they share nothing with Account A.
Without isolation, flagging Account A often cascades. The platform searches for connected accounts. It finds them through fingerprint correlation. Suddenly your entire operation is compromised.
The Cost-Benefit Analysis
What does proper account management actually cost?
Direct Costs
| Component | Monthly Cost | Annual Cost |
|---|---|---|
| Chameleon Mode Pro | $199 | $1,672 (with annual discount) |
| Residential proxies (50 IPs) | $100-300 | $1,200-3,600 |
| Total | $299-499/month | $2,872-5,272/year |
Cost of Poor Isolation
What happens without proper isolation:
| Event | Direct Cost | Indirect Cost |
|---|---|---|
| Account ban | $0 | Months of community building |
| 2FA cascade | $0 | Client trust, potential contract loss |
| Account linking | $0 | All connected accounts flagged |
| Shadowban | $0 | Unknown duration of zero reach |
One burned client account can cost more than a year of proper tooling.
Break-Even Analysis
If proper isolation saves one client relationship per year, it’s profitable.
If it saves 10 hours per month in account recovery, it’s profitable.
If it prevents one cascade where multiple accounts get linked and banned, it’s profitable.
The question isn’t whether isolation is worth the cost. It’s whether you can afford the alternative.
Implementation Checklist
Use this when setting up new accounts or auditing existing operations:
Profile Setup
- Unique profile created in Chameleon Mode
- Dedicated residential proxy assigned
- Timezone synchronized to proxy location
- Locale settings match geographic identity
- Profile tagged for organization
Account Maturation
- Profile photo uploaded
- Bio completed with relevant details
- Initial organic activity (follow, upvote, comment)
- 2+ weeks of light activity before heavy use
- Content posting started gradually
Team Configuration
- Access shared with appropriate team members
- Role permissions set correctly
- Team timezone coverage planned
- Automation schedules distributed across team
Ongoing Operations
- Session verification automated
- Activity logging enabled
- Backup accounts prepared
- Content archived externally
- Regular health checks scheduled
FAQ
Q: Can I use the same proxy for multiple Reddit accounts?
A: No. Each Reddit account needs its own proxy. Sharing proxies creates network-level correlation that’s trivial to detect.
Q: How long should I wait before using a new account for marketing?
A: Minimum two weeks of organic activity. Four weeks is safer. New accounts with immediate promotional behavior get flagged consistently.
Q: Does Chameleon Mode work on mobile Reddit and Quora apps?
A: Chameleon Mode manages browser-based access. For mobile app access, you need separate device management—which introduces additional complexity most teams don’t need.
Q: What happens to my profiles if I cancel my subscription?
A: Profiles are stored in the cloud. Downgrading may restrict access to profiles beyond your new plan’s limit, but data isn’t deleted. Upgrading again restores access.
Q: Can Reddit detect that I’m using Chameleon Mode specifically?
A: No. Chameleon Mode uses real, unmodified browsers. There’s no signature to detect. Reddit sees stock Chrome connecting through a residential IP—indistinguishable from any other Chrome user.
Q: How many accounts can one person realistically manage?
A: Depends on activity level. With automation handling routine tasks, one person can manage 30-50 accounts for monitoring and light posting. Heavy content creation limits this to 10-15.
The Bottom Line
Managing multiple Reddit accounts without linking them requires isolation at every layer—network, browser, storage, and behavior. Incognito mode and VPNs fail because they only address one layer while leaving dozens of correlation signals exposed.
The container method works because it creates true separation. Each account exists in its own environment with its own fingerprint, its own network path, and its own behavioral history.
Chameleon Mode is the only platform that achieves this with real, unmodified browsers. Everything else either fails at transport-layer detection or requires constant maintenance as detection evolves.
If you manage accounts professionally—for clients, for brands, for scaled marketing operations—the question isn’t whether to use proper isolation. It’s how long you can afford to operate without it.
Resources
- Browser Fingerprinting Explained: Electronic Frontier Foundation (https://www.eff.org/issues/fingerprinting)
- WebRTC Security Considerations: W3C WebRTC Working Group (https://www.w3.org/TR/webrtc/#security-considerations)
- Reddit Content Policy: Reddit Help (https://www.reddithelp.com/hc/en-us/articles/360043513151)
- Quora Partner Program Guidelines: Quora Help Center (https://help.quora.com/)
- Playwright Documentation: Microsoft (https://playwright.dev/docs/intro)












